“A Fully Immersive Baptism By Fire”

Notes from the Shift5 team that supported the U.S. Army’s Scarlet Dragon Oasis
FT BRAGG, NC – “My military background was a huge part of what allowed me to drive through this.” Zack Chappell credits his 22 years in the Air Force with preparing him to lead the Shift5 team that supported the U.S. Army’s Scarlet Dragon Oasis last month, although he admits, “I’m used to jumping out of planes, not really loading them.”
Addressing Cyber Defense for Vehicles and Weapon Systems: Is Your Onboard Operational Technology at Risk?

Read our latest blog to understand best practices for defending vehicles and weapon systems from cyber risk, and how onboard OT differs from IT and other traditional OT networks.
Top 3 Operational Technology Cybersecurity Takeaways from the DAFITC 2022 Event

It’s well past time to expand our notion of cybersecurity to the extended cyber terrain, which includes the onboard operational technology that powers our weapon systems and military aircraft. Read this blog from DAFITC that includes key takeaways on operational technology cybersecurity and more.
Bringing Cybersecurity to the Forefront: Thoughts from the DEF CON 30 Aerospace Village

Jeff Zacuto, Director of Product Marketing, Commercial Aviation, at Shift5, shares a few important takeaways from DEF CON 30 about the state of cybersecurity in the aerospace industry and how space now plays a larger role in our overall critical infrastructure protection.
4 Questions with Josh Lospinoso: Shift5’s ABMS ID/IQ Contract

For more on why Shift5 pursued the AMBS ID/IQ award and what it will contribute, read this Q&A with Shift5 co-founder and CEO Josh Lospinoso.
Advocating for Weapon System Cybersecurity at Reagan National Defense Forum

In December, Shift5 attended The Reagan National Defense Forum (RNDF), an annual event that brought together leaders across the defense community to assess America’s national defense policies in the context of the global threat environment.
The Cyber Attacks that Impact our Daily Lives

When most people think of cybersecurity or cyber attacks, they typically think of malicious activity targeting sensitive IT (information technology) assets. These assets often contain highly-valuable data that can be stolen, sold, or held for ransom by a motivated adversary.
Essential Technology Upgrade for DoD Fleets

(Washington, D.C) April 29, 2021 – Shift5, Inc., an operational technology data and cyber security company, has released an innovative solution for real-time predictive maintenance technology for Department of Defense weapon systems.
How Secure are DoD Weapon Systems?

DoD Weapon Systems are choc-full of digital components. They are more networked and software dependent than ever before, but generally these systems were never designed with cybersecurity in mind.
The State of DoD Weapon System Security
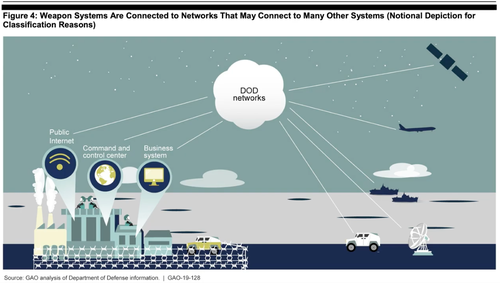
DoD Weapon Systems are choc-full of digital components. They are more networked and software dependent than ever before, but generally these systems were never designed with cybersecurity in mind.
